views
Cyber attackers and criminals are stepping up efforts to go about targeted businesses, and in what happens to be a new trend, are targeting the cyber security community in order to steal key vulnerability tools to carry out more invasive cyber breaches. The latest instance of this, reported by the Google Threat Analysis Group (TAG)’s Adam Weidemann, is a noted North Korean state-backed cyber crime ensemble, which has now set up a front called SecuriElite, and is now looking to rope in victims from the cyber security researcher community itself. The tactic takes on a new offensive note by targeting the community working to defend enterprises and consumers from cyber breaches, therefore stealing the root tools that are used to defend against the various cyber attacks that such threat actors employ.
In what is a known social engineering tactic, the advanced persistent threat (APT) group was reported by the Google TAG team in January to be specifically targeting a league of legitimate cyber security researchers. The coordinated attack saw the North Korean APT set up multiple Twitter and LinkedIn profiles, and engage in reporting on various cyber security exploits. The videos and blogs posted by these accounts initially reported vulnerabilities that were seemingly legit, but closer inspection had revealed that the attacks were already reported by security organisations, and also patched by tech majors. However, in a bid to establish trust in the security community, the attackers fabricated working concept proofs of these vulnerabilities.
The move is not entirely unprecedented – in the infamous SolarWinds data breach, Russian hackers too targeted American cyber security researchers and first responders. The threat actors had identified a list of notable figures from the cyber security community, in a cyber-political espionage move, to track what the United States department of homeland security may turn to, in order to protect their systems from being breached. As Chris Cummiskey, homeland security undersecretary had told CNN, “It shows a level of sophistication in terms of targeting those who are working actively to prevent the attacks from either occurring or expanding. The level of sophistication is problematic because they’re actually going after people that they see as more valuable.”
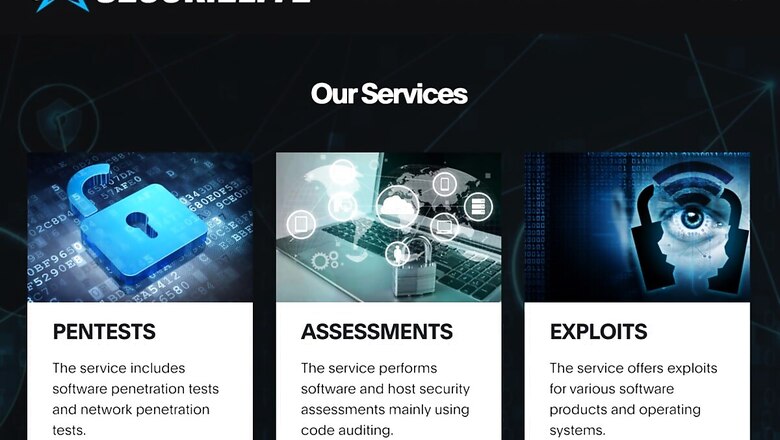
Now, in a new update to this social engineering and spear phishing attack spree, the same group of cyber attackers have now established a fraudulent security and penetration testing firm, SecuriElite. To the security researcher community, these attackers are posting their work in sync with SecuriElite, inviting legitimate researchers engaged with leading cyber security organisations to collaborate on various vulnerability testing and exploit discovery projects. The attackers would then share a Visual Studio project with the researchers, which in turn downloaded a backdoor named FallChill (or Manuscrypt) to the researchers’ devices. The FallChill backdoor has been a noted remote code execution (RCE) tool that has been deployed by the notorious Lazarus group of North Korea.
“Security researchers successfully identified these actors using an Internet Explorer 0-day. Based on their activity, we continue to believe that these actors are dangerous, and likely have more 0-days. We encourage anyone who discovers a Chrome vulnerability to report that activity through the Chrome Vulnerabilities Rewards Program submission process,” wrote Weidemann in his report on the Korean APT threat tactic, earlier this month.
What is worrying here is that the attackers are looking to snipe on the key tools that cyber security research organisations use to defend against major security breaches and newly patched zero-day flaws. The tools that are in line to be stolen include cyber assessment infrastructure, penetration test honeypots and also exploit monitors for key consumer systems. Stealing such tools can help attackers negate security systems right from scratch, therefore building even more robust exploits that can not only deceive security systems, but also add layers that are difficult to breach even for security organisations. A full list of accounts linked with the new move can be found in the Google TAG post by Weidemann, here.
Read all the Latest News, Breaking News and Coronavirus News here. Follow us on Facebook, Twitter and Telegram.


















Comments
0 comment