views
Despite all its recent apologies and hyperbolic justifications of how and why things may have gone wrong, the sheer volume of security inadequacies makes Zoom a very difficult company to trust. Now, a collaboration between an independent cyber security researcher Trent Lo, and members of SecKC in USA has revealed just how vulnerable Zoom continues to remain, and whatever security steps it has been attempted to highlight are still pretty much ineffective. To prove this, Lo and his colleagues built zWarDial, an automated tool that let them use the war dialing technique to identify open Zoom meetings and breach them.
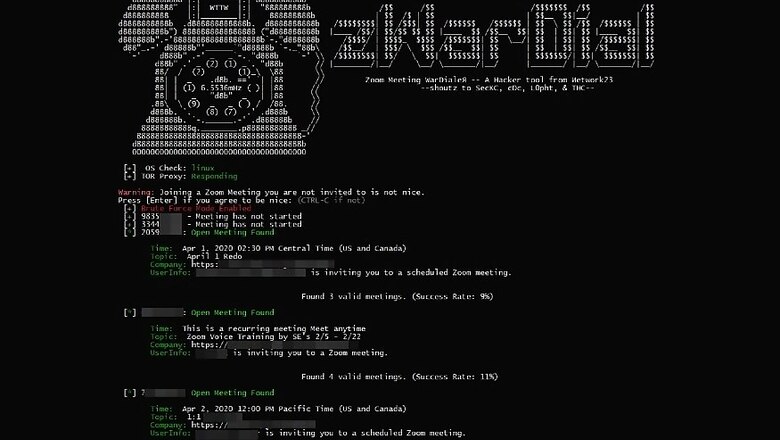
The tool uses a known technique of war dialing, which essentially attempts to brute force process a serial of numbers in order to dial bulk numbers quickly. This is particularly effective for calling on services that do not have adequate protection against such brute force techniques, and primarily use a string of numbers as the ID. zWarDial, in this case, was used to track down Zoom meeting IDs and attempt to breach them in order to get unauthorised access, which in turn explained not just how vulnerable, but also how seemingly easy it might be for malicious attackers to hack into ongoing Zoom meetings — an act that has become unduly popular as 'zoombombing'.
According to information disclosed in a report by a fellow security reporter, Brian Krebs, zWarDial could find about 110 ongoing Zoom meetings each hour, hence processing over 2,000 Zoom meetings across the world in a single day. Earlier this year, prior to become so popular, Zoom had informed Check Point Security that it had fixed a vulnerability where users could use brute force algorithms to identify Zoom meetings. zWarDial very easily nullifies the claim by simply routing its traffic access through Tor — something that is the least that an attacker would do.
That is not all — Zoom, in updated privacy policies and various statements to the media, had stated that it has updated its system in a way where all meetings are password protected by default. This, too, is clearly a skewered statement since zWarDial could find plenty of open meetings being held on Zoom, which could be accessed once the brute-forced IDs were entered on the app. Zoom does put some of the onus of the security flaws back on the user, and while as a user it is always imperative that a strong password is used for any activity online, these may pertain largely to basic users that leave default settings on.
Through zWarDial, the security researchers found that the tool returned a 14 percent success rate of identifying open meetings. With Zoom now being used by millions across the world, even the 14 percent vulnerability rate would leave million exposed to privacy breaches and data theft. In his last blog post, Zoom founder Eric Yuan had announced a three-month freeze in any new feature development and vowed to fix all security issues with his service. Going forward, it will be interesting to see how Zoom manages to fix these issues, and just how many more such vulnerabilities are found in the app.




















Comments
0 comment