views
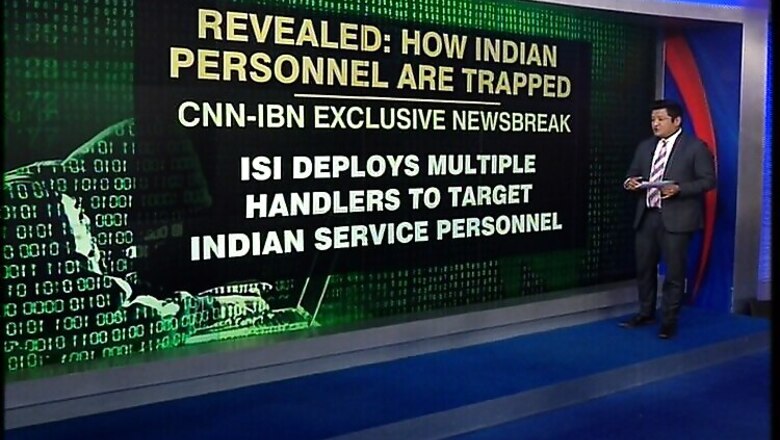
Pakistan is snooping on Indian military personnel and accessing even crucial information on counter terrorism operations using a spyware, a CNN-IBN investigation has revealed.
The investigation showed that Pakistani agency Inter-Services Intelligence (ISI) is using a malicious software to infect the smartphones and personal computers of military personnel.
The spyware app SmeshAPP, which is easily available on Google playstores, steals all the information stored --including phone calls, text messages and photographs -- and tracks his geo coordinates.
The information is stored on a server located in Germany and is hosted by a man identified as Sajid Rana, who is based out of Karachi.
The investigation showed, that using this method, Pakistan handlers were even getting crucial information on the movement of troops following the terror attack on the Indian Air Force base in Pathankot in January 2016.
The soldiers are lured through Facebook accounts by honeytraps set by ISI. It is learnt that more than 10 such fake FB profiles are are now being used and that dozens of Indian military personnel are now unknowingly in touch with Pakistani handlers.
The three services of the armed forces - Army, Navy and Air Force - apart from the Border Security Force (BSF) and Central Industrial Security Force (CISF) are so targeted. The handlers identify 'soft'targets before trying to lure them. While field-level officers are the prime targets, even retired personnel are not spared.
To investigate the malicious link, CNN-IBN downloaded this app on a mobile phone. The app showed it was developed by a company called smeshapp.com, but the internet address did not yield any result.
Further analysis revealed that this app throws up connection to a server named pbxmobiflex.com, which is registered in the name of Sajid Rana.A search for his listed number in the open source directory TrueCaller which fetched the result as Ayan Butt.
With technical help we entered the system and it opened the storehouse of individual soldiers personal and professional information. Their entire contact list was seen, SMS records and photogallery could be accessed and calls could be recorded.
Also the app could be used to start a recording of audio and video, almost taking over the phones of the service personnel by remote.
Security agencies were recently alerted about a twitter handle based in Karachi tweeting pictures of the Pampore anti-terror operations as well as of the BSF personnel killed in an encounter with Maoists in deep forests of Chhattisgarh.
The pictures were taken by fellow soldiers, and since no media outlet got access to them , it was clear that the information was being accessed.



















Comments
0 comment