views
Improving Online Security
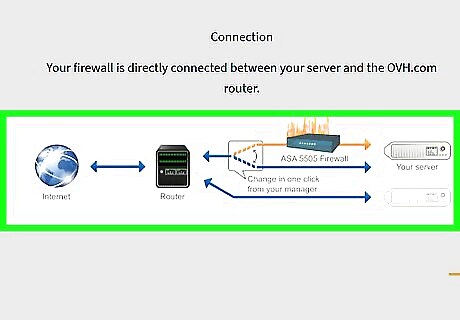
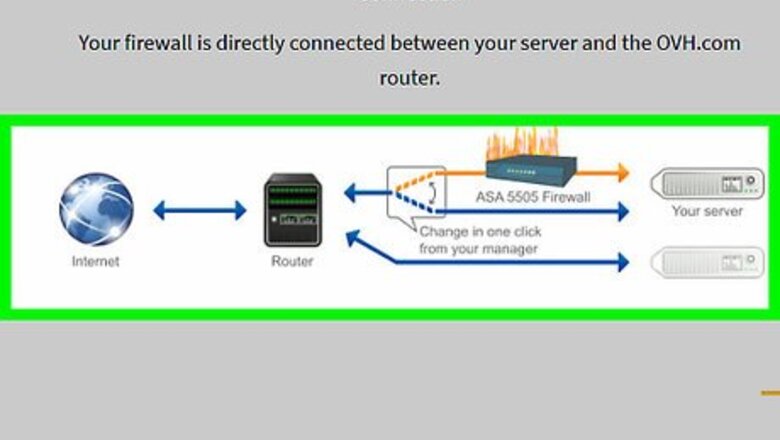
Invest in a firewall. After establishing your server, the next immediate thing you need to do is to put up a firewall. Firewalls are programs the filter out the information that goes in and out of your computer. There are a lot of firewall applications available on the Internet and from local computer stores, but even the less experienced hackers can get past these. Invest in a well-developed and reputable application to ensure the utmost security. Firewalls are installed just like any other programs and are more than capable of protecting small scale servers. But if you’re running several mainframes, enterprise firewalls need to be installed by a software security specialist.
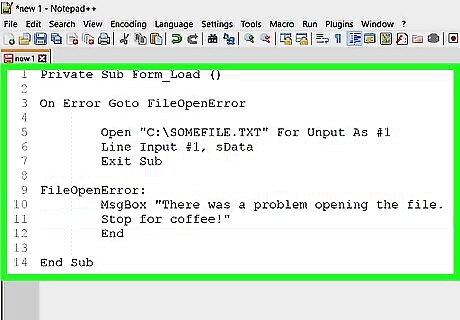
Protect your codes. When creating your program codes for applications that your intended end users interact with, make sure that appropriate error trappings are placed within the application. Hackers typically use SQL injections or the manipulation of an application’s code through its URL or SQL forms. When your program lacks error trappings that can cover loopholes where SQL queries can be injected, your server becomes a sitting duck to hackers.
Use an SSL. SSL, or Secure Sockets Layer, is an Internet security protocol that protects your server by making sure that all information that goes in and out of the system remains private and inaccessible to third-party users. Hackers can easily get the information from your server if it does not ask an SSL certificate. You can take advantage of this technology for your server by visiting the SSL website (http://info.ssl.com/) and availing its service.
Limit uploads. Your server will need to accept data from end users in order for it to gather information. Though uploads are necessary, you still need to limit the amount of information going into the system. To do this, format forms properly to make sure that only the required data gets into the system.
Use passwords. Passwords are the most basic tool you can use and your first line of defense in protecting your server from hackers. Using passwords restricts any unauthorized access to your system; those without extensive technical know-how will find it hard to get into your system. Make sure that the password you make is complex and very hard to crack. Using combinations of special characters, mixed cases and numbers will make it harder to break.
Preventing Physical Access
Keep your server’s location secret. If you can, avoid divulging the physical location of your server. Hackers that cannot get through to your digital security will most likely resolve to direct physical access to your mainframe.
Limit access. If you can’t keep your server’s location confidential, especially for offices and businesses where the addresses are intentionally given out to people, make sure that only authorized personnel has access to the server room. Lock your server in a closed, cool, and suitable room, and provide security keys only to those that need to have access.
Avoid giving out any digital information about your server. Hackers can easily break into your system servers just by knowing its IP addresses. Make sure that these kinds of digital information about your server remain confidential and on a need-to-know basis only.
Hire a professional. There are many IT professionals that specialize in network and Internet security. If you find that your technical knowledge is limited and if your budget permits, employ a security specialist to take care of protecting your server from hackers for you. Salaries of these kinds of personnel range from a few thousand to even hundreds of thousands of dollars, depending on the skill level. Though it may sound costly, it will prove to be worth it, especially if you’re housing very valuable information on your servers.



















Comments
0 comment